In Colombia, PUMA is not what it seems
by Digital Rights LAC on August 24, 2015
The Hacking Team leak confirmed that Colombia purchased in 2013 the remote control software known as “Galileo” for PUMA (the country’s surveillance platform), thus strengthening their surveillance capacities, but what is this improvement?
Pilar Sáenz and Carolina Botero, Fundación Karisma
In 2014, the Citizen Lab report showed that the Colombian government could be a Hacking Team client. However, besides the suspicion on the use of exploits (software pieces or scripts placed in other archives or websites that take advantage of the vulnerability to get into the computers) and the identification of an address in Colombia where the information associated with these intrusions was being sent, we knew little about the use of this technology in the country.
With the Hacking Team documents, now we know more details about the technology; we know that Galileo is a program that works through a malicious software, malware or spyware, infecting the computer or mobile of the attacked person. It is not like any other malware: it is a tailor-made exploit, customized, that does not need the user’s click to run; it’s enough to visit the infected webpage or open a file that is not even suspicious. Once the device is infected, the attacker may abusively gain access to the computer or mobile to get data, messages, calls and emails secretly. He also gets access to the microphone, camera and the computer or mobile keyboard register, and therefore, leaving the information of the target in a vulnerable position.
We know that it was acquired in Colombia by the National Police Office (DIPON) through two contracts made with intermediaries, not with the Hacking Team, as the police later admitted. The first one was with Robotec in 2013, valid until 2016; the second one was a hiring process that was almost closed by the time of the leak, and if materialized, would be until 2018 and the contractor will be the Israeli company NICE. Precisely, the police unlinked themselves from Hacking Team by saying their contracts are with Robotec, however, in the leaks there are emails asking for exploits in order to use them in 2015’s first semester. These mails were sent from police accounts and were directed to the technical assistance service from Hacking Team, since they are who supply those exploits.
Of the many analysis perspectives of this information, there is one that really draws our attention: both contracts were made with funds intended to strengthen the Unique Platform of Monitoring and Analysis (PUMA), that in 2013 was already in the public eye because of its invasive ability in Colombian’s intimacy, and that we still did not know anything about its relation with Galileo.
PUMA is a technological platform assigned to the Directorate of Criminal Investigation and Interpol (DIJIN), which aims to register and verify information about people connected with judicial investigations and coordinate police tasks, district attorneys and even phone companies. PUMA is named for the first time in one resolution from 2007 and it replaced the old platform on interception of communications called Esperanza. We have been told that it is only used to spy on people linked with judicial processes and it is made through the intermediaries, phone companies or the internet service providers.
What do the leaks about the abilities of Puma tell us?
The leaked information helps to establish the capacities that Puma will have in 2015: not only it would inspect Colombia’s communications traffic by intercepting the target’s comms, but it would also increase its capacity to appropriate the target’s device, control it and find everything that is there or in the surroundings.
This abilities are described in five leaked documents: the commercial proposal made by Hacking Team to NICE System related to the Remote Control System – Galileo, reserved for DIPON Colombia (June 23rd, 2015), and the manuals for the administrator, the analyst, the technician and the system administrator for Galileo.
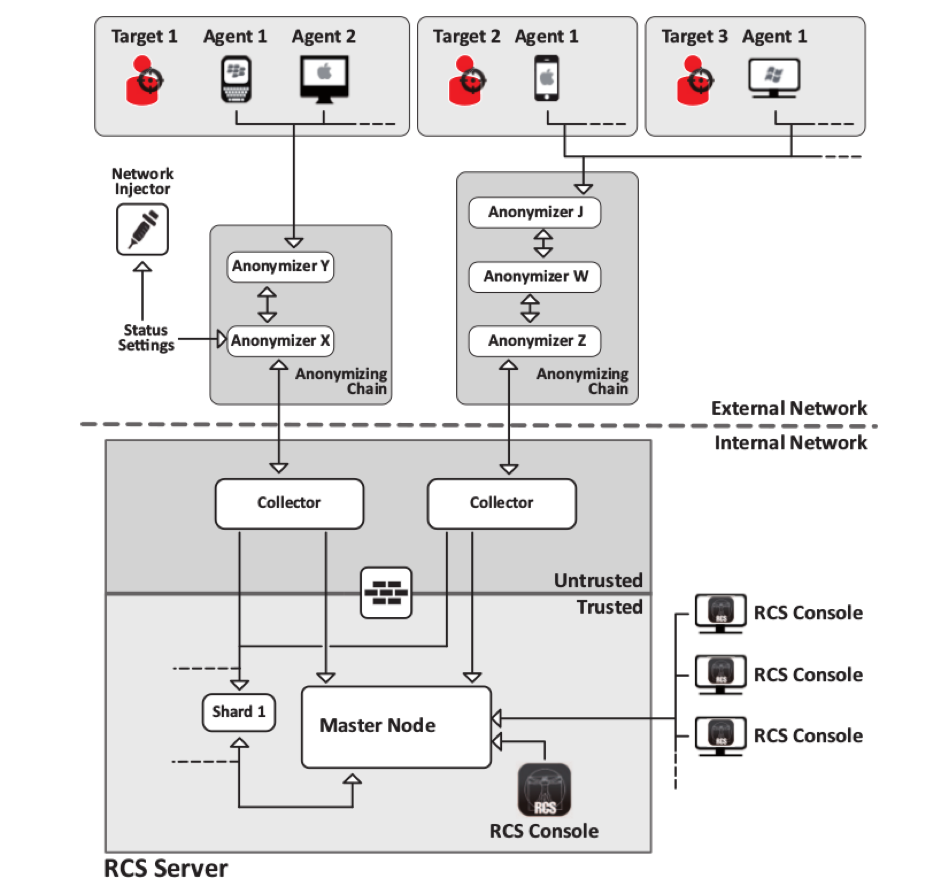
According to the document in the proposal, the Remote Control System software that was going to be purchased includes: a master node and two collectors, six anonymizers, 50 operational agents and 10 consoles for users, which constitute the system infrastructure. This would include licenses for seven platforms (Windows, Mac, Linux, Blackberry, Android, iOS and Windows Phone), besides vectors for physical infection (USB), in networks (WI-FI and LAN), remotes (for Android and Blackberry) and a 3-year subscription to the service of exploits deliverance.
To explain the design of the system infrastructure, let us take the diagram of the architecture found in the system administrator manual:
When the software in used in an investigation, an operation is defined and a series of targets are selected. For each of these goals or targets, one or many agents are selected, the devices that will be taken under control. The platform to be used and the attack form are defined depending according to the devices and their operating system (almost any device would be included, judging by the licenses being sought to acquire). The form of the attack is defined by the potential kind of access to the device: customized exploits, created for the target, disguised in an archive that the same users of the system prepared with the direct help from the Hacking Team’s technical support.
The infection methods are detailed in the technician’s manual and include physical infection using USB memory, CD or documents; or remote infection executing an archive transferred over the internet. The evidence, that is to say, the information gotten from the infected computers, could be collected physically or over the internet. Even computers that will never connect to the net could get compromised.
The infecting files were solicited to the Hacking Team support team by sending them a clean archive (a .docx document that could be the invitation to an event, a flyer, a Power Point presentation, an app for Android; any excuse is valid). By return, a customized exploit was received: a file or an url address where the malware was inserted. In fact, there are several e-mails made public after the leak, where the exploit requests to the “Hacking Team” support team from a National Police agent can be read.
Once the device is compromised (the selected target opened the archive or clicked the infected link), the information capture starts. The capture is made over the net using anonymizers, that are similar in their structure to the Tor network. This equipment creates a chain of connections where the information goes through in a way that, in principle, can make the attacker anonymous; this is, if the attacked target realizes the infection, he cannot trace the attacker.
The information reaches the internal network of the platform (PUMA) through the collectors, and from there to the master node. The processing and visualization of the stolen information is made through the consoles connected to this node. Once the information is collected, the agent deletes itself from the device remotely.
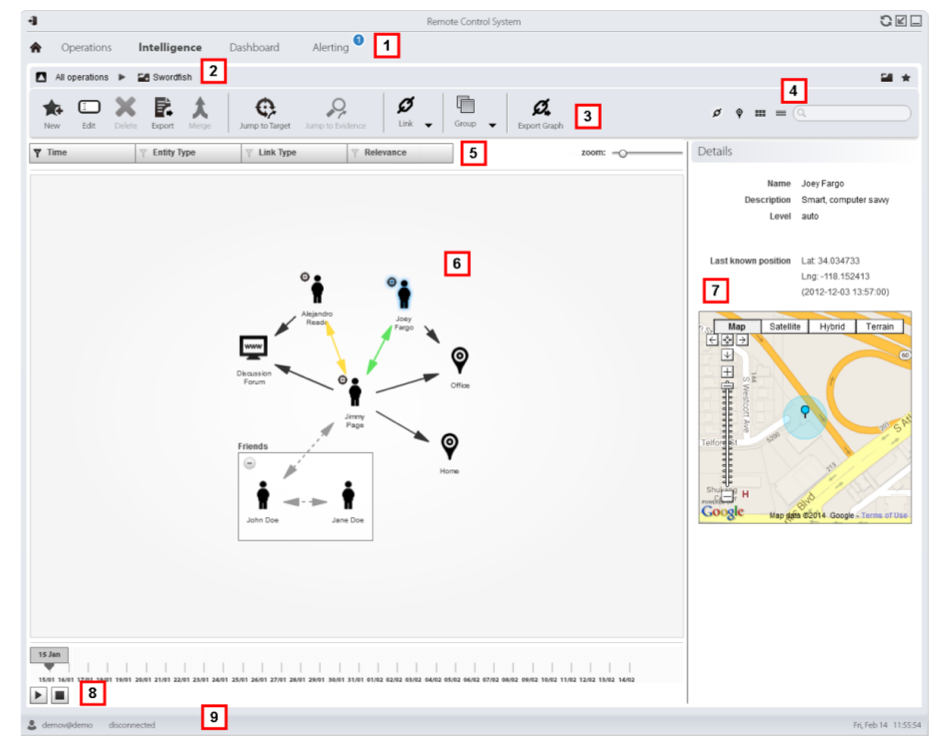
Once the information about the persons and places related to the investigación is gathered, it is processed, stored, and analyzed. From their consoles, the analysts could monitor the target, explore the compromised devices, and analyze the evidence and export it.
Persons under investigation as well as other persons and places (physical and virtual) involved in the investigation are represented by entities. Both the relations between persons as the relations between persons and places are represented by links between entities.
The visualization of links shows the quantity, direction and frequency of the evidence that defines the links between the entities.
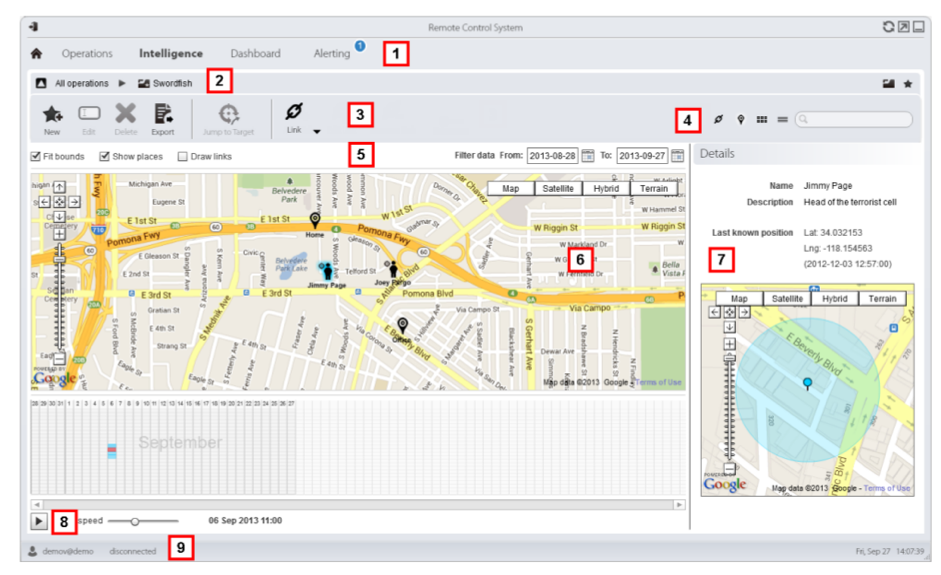
The other possible visualization by the system is the position one, showing in a map the entities for an operation and its links. In this view, it is even possible to see the target’s movement over time.
Puma is not what it seems
In 2013, PUMA got linked to a media scandal when it became public that the police was increasing its capacities. Attempts were made to establish what the platform was for, and how it adjusted to the legal frame; it was said the law had ordered that the telephone companies and the internet service providers should allow PUMA to have direct access to their traffic, as Snowden accused months before. Despite it was a technical capacity that was legally destined exclusively to the penal investigation, without the identification of its equivalent for intelligence investigation, the question of whether the same capacity applies in both scenarios persists.
In the absence of clarity, we should stay in the established: the operation of PUMA is responsibility of the Prosecutor’s office, who uses it in penal investigations that should be authorized by a judge (it can do it without authorization when time is short, but go to obtain authorization later), and is managed by the police.
In this context, PUMA has been a source of tension between both agencies. During the media debate in 2013, the Prosecutor’s office suspended its start (to replace Esperanza) because it considered that it could lead to abuses, and reaffirmed that its use was limited to judicial investigations. However, the leaked e-mails deny the suspension of PUMA; in the discussion about the technology that the police would buy this year, they wrote about including specific exploits for attacks during the first semester of 2015. What is the actual situation? Is PUMA working or no? Are the institutions collaborating?
In 2013, while the Colombians discussed about the reach of the PUMA’s communications interceptions with outrage, the police hired a enhancement of their surveillance capacities with Robotec; not to be distant witnesses of the suspicious activities merely, but to allow the watchers to infiltrate and directly know everything about their suspects.
The capacity of intromission of these tools in the intimate life of the persons beyond the access of their communications is what constitutes the distribution and use of malware and the hack of computer systems as a crime, making us question: is legal its use for surveillance authorities?, and if so, how should they be used to avoid improper use from public servants?
After all, “according to the international standards, the use of surveillance software or systems in the private communications should be established clearly and precisely in the law, be truly exceptional and selective, and limited by the strictly necessary for the fulfilling of imperative goals such as the investigations of felonies defined by the legislation”, as told by the OAS Special Rapporteur for Freedom of Expression, Edison Lanza, in a recent statement about the Hacking Team case.
The fact that, two years later, the capacities of PUMA are yet unclear speaks ill of the intelligence systems transparency in a country so-called democratic. Considering the record of abuses of the intelligence capacities in Colombia, materialized in scandals as the chuzadas or the Andrómeda case, is also worrying that we don’t even have someone to complain to.
The Colombian intelligence law has a lot to improve in the protection of the Colombians rights, especially on balance and control mechanisms where little has been done; and the final instance, the Commission for Monitoring the Intelligence Law in the Congress, is not even working because its members have not obtained yet the approval of the Intelligence office, even though the Congress took office one year ago. Is there any paradox more illustrative than this about the necessity of human rights considerations in the Colombian Intelligence?